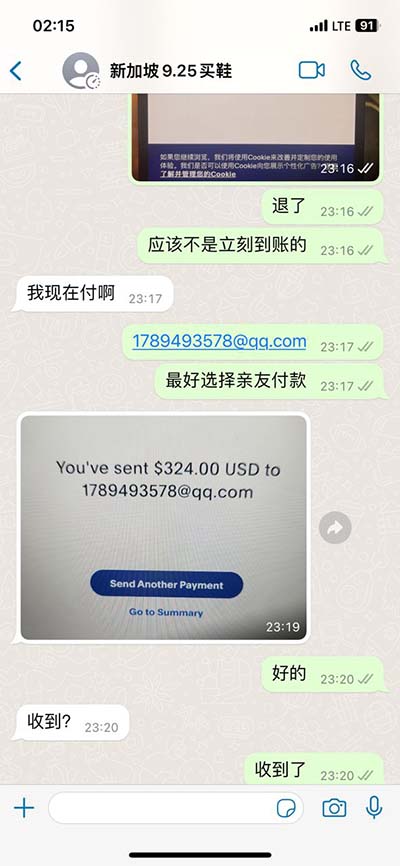
boot sector virus elk cloner An ingenious piece of primitive malware, Elk Cloner wasn’t quite the unpredictable and uncontrollable virus one might imagine. When infecting a new device, it imprinted a . Details. Security. Rolex Datejust Oysterquartz. Silver Dial "First Generation" 17000. $ 6,611. + $111 for shipping. NL. Rolex Datejust Oysterquartz. Silver Dial Ref. 17000 Year 1978. $ 6,610.
0 · how to delete elk cloner
1 · elk cloner wiki
2 · elk cloner virus
3 · elk cloner infection
$3,781.00
how to delete elk cloner
ysl libre'' nas?l okunur
The boot sector virus was written for Apple II systems, the dominant home computers of the time, and infected floppy discs. If an Apple II booted from an infected floppy disk, Elk Cloner became . Elk Cloner is one of the first known microcomputer viruses that spread "in the wild", created by Rich Skrenta in 1982 as a prank. It was a boot sector virus that attached itself . An ingenious piece of primitive malware, Elk Cloner wasn’t quite the unpredictable and uncontrollable virus one might imagine. When infecting a new device, it imprinted a . The virus targeted the boot sector of various storage media including HDDs, SDDs, flash drives, and floppy discs. Once an Apple II system booted from an infected disc, Elk Cloner permanently embedded itself into the .
Elk Cloner, 1982: Viewed as the first virus to hit personal computers worldwide, Elk Cloner spread through Apple II floppy disks and displayed a poem written by its author, a ninth .
"Elk Cloner"— self-replicating like all other viruses— bears little resemblance to the malicious programs of today. Yet in retrospect, it was a harbinger of all the security . Richard Skrenta’s “Elk Cloner” was 400 lines long and disguised as an Apple boot program. Described by its author as “some dumb little practical joke,” the virus attached itself to the Apple DOS 3.3 operating system and .An example of one type of Apple II malware was called “Elk Cloner”, it was created by Richard Skrenta a 15-year-old high school student. It infected the systems using the “boot sector” technique which means that if the user booted .Elk Cloner spread by infecting the Apple DOS 3.3 operating system using a technique now known as a boot sector virus. It was attached to a program being shared on a disk (usually a game).
Elk Cloner is a boot sector virus that invades a computer's hardware. It was written for Apple II systems in assembly language and infected floppy disks. In addition to infecting its host computer, the virus could also automatically copy itself to other computers via an infected floppy disk.
The boot sector virus was written for Apple II systems, the dominant home computers of the time, and infected floppy discs. If an Apple II booted from an infected floppy disk, Elk Cloner became resident in the computer’s memory. Elk Cloner is one of the first known microcomputer viruses that spread "in the wild", created by Rich Skrenta in 1982 as a prank. It was a boot sector virus that attached itself to the Apple II operating system and spread through floppy disks. An ingenious piece of primitive malware, Elk Cloner wasn’t quite the unpredictable and uncontrollable virus one might imagine. When infecting a new device, it imprinted a signature byte to the host’s disc directory to show that a particular operating system had .
elk cloner wiki
The virus targeted the boot sector of various storage media including HDDs, SDDs, flash drives, and floppy discs. Once an Apple II system booted from an infected disc, Elk Cloner permanently embedded itself into the system’s memory. Elk Cloner, 1982: Viewed as the first virus to hit personal computers worldwide, Elk Cloner spread through Apple II floppy disks and displayed a poem written by its author, a ninth-grade. "Elk Cloner"— self-replicating like all other viruses— bears little resemblance to the malicious programs of today. Yet in retrospect, it was a harbinger of all the security headaches that. Richard Skrenta’s “Elk Cloner” was 400 lines long and disguised as an Apple boot program. Described by its author as “some dumb little practical joke,” the virus attached itself to the Apple DOS 3.3 operating system and spread by floppy disk.
An example of one type of Apple II malware was called “Elk Cloner”, it was created by Richard Skrenta a 15-year-old high school student. It infected the systems using the “boot sector” technique which means that if the user booted up their system from an infected Floppy Disk, a copy of the virus was placed in the memory of the computer.
Elk Cloner spread by infecting the Apple DOS 3.3 operating system using a technique now known as a boot sector virus. It was attached to a program being shared on a disk (usually a game).Elk Cloner is a boot sector virus that invades a computer's hardware. It was written for Apple II systems in assembly language and infected floppy disks. In addition to infecting its host computer, the virus could also automatically copy itself to other computers via an infected floppy disk.
The boot sector virus was written for Apple II systems, the dominant home computers of the time, and infected floppy discs. If an Apple II booted from an infected floppy disk, Elk Cloner became resident in the computer’s memory. Elk Cloner is one of the first known microcomputer viruses that spread "in the wild", created by Rich Skrenta in 1982 as a prank. It was a boot sector virus that attached itself to the Apple II operating system and spread through floppy disks. An ingenious piece of primitive malware, Elk Cloner wasn’t quite the unpredictable and uncontrollable virus one might imagine. When infecting a new device, it imprinted a signature byte to the host’s disc directory to show that a particular operating system had . The virus targeted the boot sector of various storage media including HDDs, SDDs, flash drives, and floppy discs. Once an Apple II system booted from an infected disc, Elk Cloner permanently embedded itself into the system’s memory.
Elk Cloner, 1982: Viewed as the first virus to hit personal computers worldwide, Elk Cloner spread through Apple II floppy disks and displayed a poem written by its author, a ninth-grade. "Elk Cloner"— self-replicating like all other viruses— bears little resemblance to the malicious programs of today. Yet in retrospect, it was a harbinger of all the security headaches that.
Richard Skrenta’s “Elk Cloner” was 400 lines long and disguised as an Apple boot program. Described by its author as “some dumb little practical joke,” the virus attached itself to the Apple DOS 3.3 operating system and spread by floppy disk.


And in 1974, when the Constellation Marine Chronometer was introduced, it had been certified as a “Marine Chronometer” with a routine variation of fewer than 0.002 seconds per day. Until this day, it makes it the only wristwatch ever to receive this extraordinary distinction.
boot sector virus elk cloner|elk cloner wiki